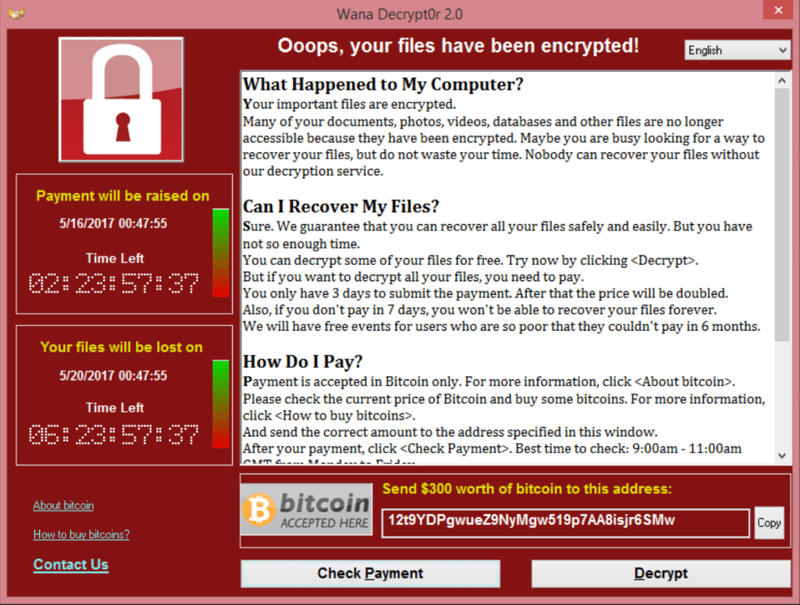
WannaCry was a type of malware that caused a large-scale ransomware attack in May 2017. The malware spread through a computer network exploiting a vulnerability in Microsoft Windows operating system that had been previously discovered by the NSA and leaked online.
WannaCry exploited a vulnerability in Microsoft Windows known as EternalBlue, which was initially discovered by the US National Security Agency (NSA) and then leaked online by a group of hackers called Shadow Brokers in April 2017. The vulnerability exists in the Windows Server Message Block (SMB) protocol, which is used for file and printer sharing on a network.
The EternalBlue exploit works by sending a specially crafted packet to a vulnerable computer’s SMB service, which allows an attacker to execute remote code on the targeted system. Once the attacker gains control of the computer, WannaCry uses a combination of techniques to spread to other vulnerable computers on the same network, including the use of a backdoor called DoublePulsar.
What made WannaCry particularly dangerous was its ability to spread rapidly through networks, including those that were not up-to-date with the latest security patches. Microsoft had released a patch for the EternalBlue vulnerability in March 2017, but many organizations had not yet applied the patch at the time of the attack. This allowed WannaCry to infect hundreds of thousands of computers around the world in just a few days.
Once it infected a computer, WannaCry encrypted the user’s files and demanded a ransom payment in exchange for the decryption key. The attack affected hundreds of thousands of computers in over 150 countries, including the UK’s National Health Service, which had to cancel operations and appointments as a result. Although the attack was eventually halted, it highlighted the need for better cybersecurity measures and raised awareness about the dangers of ransomware attacks.
WannaCry was stopped by a combination of efforts from cybersecurity researchers and law enforcement agencies. A young cybersecurity researcher, known by the pseudonym MalwareTech, accidentally discovered a “kill switch” in the code of the malware. By registering a domain name that the malware was programmed to check before executing, he was able to stop the spread of the malware. This allowed cybersecurity researchers to analyse the malware and develop tools to remove it from infected computers.
Law enforcement agencies also played a role in stopping WannaCry by tracking down the individuals responsible for the attack. In December 2017, the US Department of Justice charged a North Korean hacker with the WannaCry attack, along with other cybercrimes. Although the hacker has not been extradited to the US to face trial, the charges sent a message to other cybercriminals that their actions would not go unpunished.